Earlier, on Friday, Microsoft disclosed that Iranian hackers had “sent a spear phishing email in June to a high-ranking official on a presidential campaign.” While Microsoft did not identify the specific campaign targeted and declined to comment further, the Trump campaign drew a connection between this incident and their own breach.
Donald Trump also wrote on Truth Social: “We were just informed by Microsoft Corporation that one of our many websites was hacked by the Iranian Government – Never a nice thing to do! They were only able to get publicly available information but, nevertheless, they shouldn’t be doing anything of this nature. Iran and others will stop at nothing, because our Government is Weak and Ineffective, but it won’t be for long. What Iran doesn’t realize is that I will make the World a better and safer place, and that’s good for them, also!”
FILE- Iranian schoolboys chant slogan while holding an effigy of U.S. President Donald Trump in an annual gathering in front of the former U.S. Embassy marking the anniversary of its 1979 takeover in Tehran, Iran, on Nov. 4, 2017. Iran will elect a new president Friday, June 28, 2024, after the death of hard-line President Ebrahim Raisi. Whoever takes the helm in the country will inherit Iran’s rapidly advancing nuclear program, which now enriches uranium closer than ever to weapons-grade levels. (AP Photo/Vahid Salemi, File)
Steven Cheung, a spokesperson for the Trump campaign, stated, “These documents were obtained illegally from foreign sources hostile to the United States, intended to interfere with the 2024 election and sow chaos throughout our democratic process.”
Cheung further linked the timing of the breach with a Microsoft report that noted Iranian hackers had compromised an account of a “high-ranking official” on a US presidential campaign in June 2024, coinciding with the close timing of Trump’s selection of a vice-presidential nominee. However, Cheung did not disclose whether the campaign had been in contact with Microsoft or law enforcement about the breach, stating the campaign would not discuss such conversations.
Microsoft report on sabotage
In light of these events, Microsoft’s latest report from the Microsoft Threat Analysis Center (MTAC) sheds further light on the increasing involvement of foreign actors, particularly Iran, in cyber-enabled influence operations targeting the 2024 US presidential election. The report is the third in a series by MTAC, following earlier findings on activities by Russia and China. Microsoft emphasized that their goal in sharing this intelligence is to help voters, government institutions, and political campaigns protect themselves from such threats and to underscore the importance of combating election-related disinformation.
An Iranian network known as Storm-2035, consisting of four websites posing as news outlets, is actively engaging US voter groups at opposite ends of the political spectrum. These sites are spreading polarizing messages on topics such as the US presidential candidates, LGBTQ rights, and the Israel-Hamas conflict. This network is part of a larger campaign that has been in operation since at least 2020, encompassing more than a dozen covert news sites targeting audiences in French, Spanish, Arabic, and English with social and political content.
In 2022, one of these sites, EvenPolitics, which had been publishing articles related to the 2022 US midterm elections. Although an inauthentic amplification network promoting this website was dismantled by the X platform in 2022, EvenPolitics remains active, currently publishing around ten articles per week.
A more recently established site, Nio Thinker, began publishing in late October 2023. Initially focusing on the Israel-Hamas conflict, its content has increasingly shifted towards the US elections. Nio Thinker caters to liberal audiences and includes sarcastic, lengthy articles that criticise Donald Trump, describing him with phrases like “opioid-pilled elephant in the MAGA china shop” and “raving mad litigiosaur.”
Another site, Savannah Time, claims to be a “trusted source for conservative news in the vibrant city of Savannah.” This site focuses heavily on Republican politics and LGBTQ issues, particularly gender reassignment. While the Microsoft Threat Analysis Center (MTAC) has not yet observed significant social media amplification of these sites, it is possible this could increase as election day approaches.
MTAC has found evidence suggesting that these sites are using AI-enabled services to plagiarize content from US publications. Analysis of the webpage source code and indicators within the articles themselves suggest that the operators of these sites are likely employing SEO plugins and other generative AI tools to create article titles, keywords, and automatically rephrase stolen content. These tactics are intended to drive search engine traffic to their sites while obscuring the content’s original sources.
You’ve got mail
On July 22, POLITICO started receiving emails from an AOL email address from an individual who identified as “Robert”. Over the following weeks, the sender shared what appeared to be internal communications from a senior Trump campaign official. Included among these documents was a research dossier dated February 23, on Trump’s running mate, Ohio Senator JD Vance. According to two people familiar with the matter, the documents are authentic, and the dossier was described as a preliminary version of Vance’s vetting file. The 271-page document contained publicly available information on Vance’s past record and statements, with some sections identifying his past criticisms of Trump as “POTENTIAL VULNERABILITIES.” The anonymous sender also shared part of a research document on Florida Senator Marco Rubio, who was another finalist for the vice-presidential nomination.
When asked how they obtained the documents, the anonymous source responded, “I suggest you don’t be curious about where I got them from. Any answer to this question will compromise me and also legally restricts you from publishing them.”
The scope of the breach remains unclear, but it represents a significant security lapse for Trump’s campaign. Last month, reports emerged suggesting that the US intelligence community had increasing evidence of Iranian plots to kill Trump in retaliation for the assassination of Iranian military officer Qassem Soleimani in 2020. Although there is no indication that the individual who targeted Trump at a recent rally was connected to this plot, the Trump campaign cited these reports in its statement. Cheung asserted, “The Iranians know that President Trump will stop their reign of terror just like he did in his first four years in the White House.”
What do we know about the campaign?
“Today, we’re sharing intelligence about activities we’ve been tracking that increasingly point to Iran’s intent to influence this year’s US presidential election,” Microsoft wrote on August 9. In recent weeks, Microsoft observed groups connected with the Iranian government escalating two types of activities. “Firstly, they’ve laid the groundwork for influence campaigns on trending election-related topics and begun to activate these campaigns in an apparent effort to stir up controversy or sway voters—especially in swing states,” Microsoft stated. “Secondly, they’ve launched operations designed to gain intelligence on political campaigns and help enable future influence attempts.”
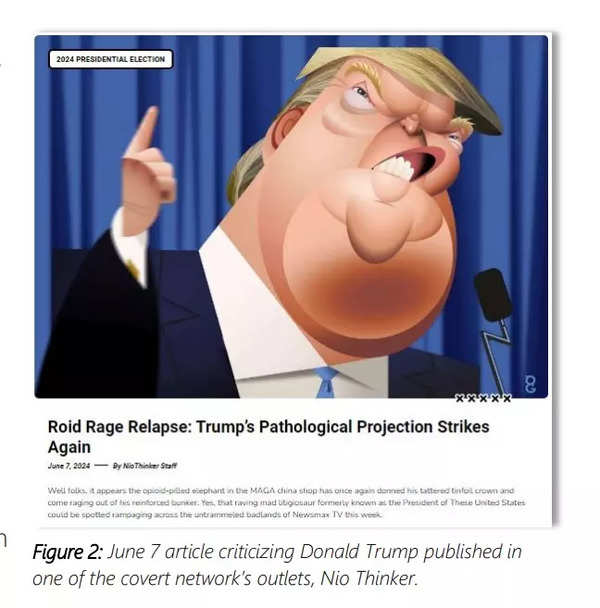
Screenshot of an article criticising Donald Trump (Source: Microsoft)
In a new report released today, Microsoft detailed this activity, highlighting four examples of what can increasingly be expected from Iran as the November election approaches. According to Microsoft, one Iranian group has been launching covert news sites aimed at US voter groups on opposing ends of the political spectrum. “One of the sites, called Nio Thinker, caters to left-leaning audiences, with content that insults former President Donald Trump,” Microsoft explained. Another site, Savannah Time, “claims to be a ‘trusted source for conservative news in Savannah’ and focuses on topics including LGBTQ+ issues and gender reassignment.” Microsoft’s evidence suggests that these sites are using AI-enabled services to plagiarize at least some of their content from US publications.
A separate Iranian group “has been setting the groundwork for US-focused influence operations since March,” Microsoft revealed. “We believe this group may be setting itself up for activities that are even more extreme, including intimidation or inciting violence against political figures or groups, with the ultimate goals of inciting chaos, undermining authorities, and sowing doubt about election integrity.”
Yet another, connected with the Islamic Revolutionary Guard Corps (IRGC), “sent a spear phishing email in June to a high-ranking official on a presidential campaign,” Microsoft reported. The email, sent from the compromised account of a former senior advisor, “contained a link that would direct traffic through a domain controlled by the group before routing to the legitimate website.” Days later, “the same group unsuccessfully attempted to log into an account belonging to a former presidential candidate.” Microsoft has since notified those targeted.
A fourth Iranian group “compromised an account of a county-level government employee in a swing state,” according to Microsoft. This compromise was part of a broader password spray operation, and Microsoft Threat Intelligence “did not observe the actor gain additional access beyond the single account, making it hard to discern the group’s ultimate objectives.” Since early 2023, the group’s operations “have focused on strategic intelligence collection, particularly in satellite, defense, and health sectors, with some targeting of US government organizations, often in swing states.”
The Microsoft Threat Intelligence Report, released by the Microsoft Threat Analysis Center (MTAC), “tracks influence operations from specific nation-state groups around the world,” Microsoft noted. MTAC “routinely tracks threats to elections as part of Microsoft’s broader Democracy Forward work,” and the latest update “builds on work the team did to track threats to recent elections in India, the UK, and France.” Additionally, Microsoft’s report includes “activities observed by actors advancing the geopolitical goals of Russia and China, each with varying degrees of effectiveness.”
Microsoft stated, “We share intelligence like this so voters, government institutions, candidates, parties, and others can be aware of influence campaigns and protect themselves from threats.” Microsoft also mentioned that they have been “training candidates and parties involved in elections this year, building on our longstanding offerings, like AccountGuard.” The company clarified, “Microsoft will not endorse a candidate or political party. Our goal in releasing these reports is to underscore the importance of combating election deepfakes and promoting education and learning about possible foreign interference.”
The report by MTAC, titled “Iran Steps into US Election 2024 with Cyber-Enabled Influence Operations,” highlights the increasing involvement of foreign nations, particularly Iran, in cyber-enabled influence operations targeting the upcoming 2024 US presidential election. This report is the third in a series by MTAC and follows earlier reports detailing activities by Russia and China.
